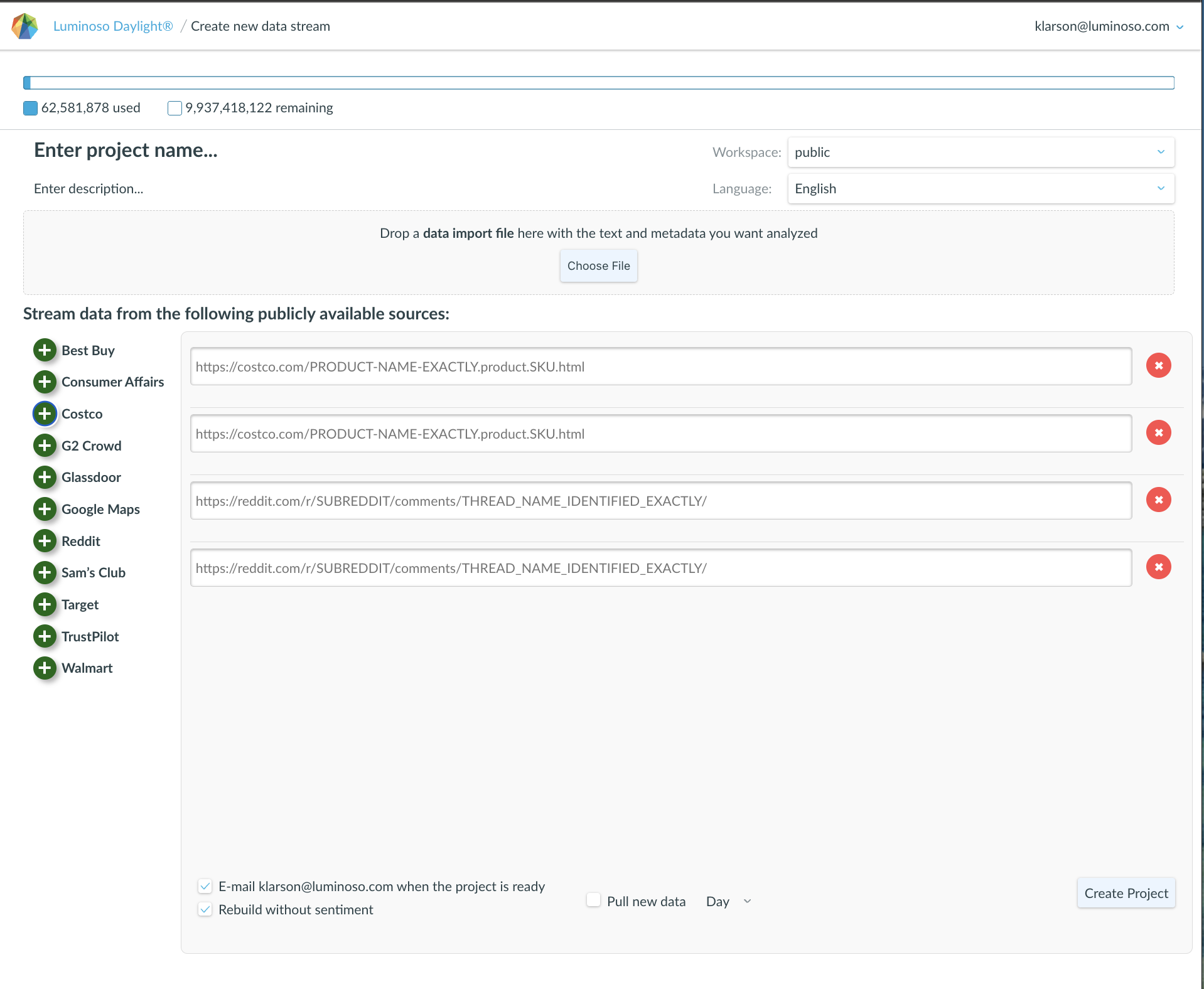
General Daylight Application Security
Data Anonymization or Hashing:
Question:
Are any anonymization or hashing techniques applied to customer data before or during processing?
Answer:
Clients have the option to anonymize or redact identifying fields prior to upload via preprocessing pipelines or through Luminoso’s API ingestion workflows. This step is strongly encouraged for any free-text fields that may contain PII or regulated identifiers.
Ingestion Safeguards:
- During data ingestion, metadata fields (e.g., user IDs, email addresses) can be hashed or removed entirely, depending on integration configurations.
- Structured metadata fields may be configured to exclude sensitive values from being retained in persistent storage.
Internal Processing and Data Access Controls:
- Luminoso’s core analytics engine is designed to operate independently of user identity, focusing on the semantic structure of textual data rather than any identifiers.
- Access to raw input data is limited via role-based controls, and only named, authorized personnel can access untransformed inputs when absolutely necessary.
Environment-level Safeguards:
- Data at rest is encrypted using industry-standard methods.
- Logs and audit trails exclude customer content and are anonymized to the extent feasible.
Optional Data Retention Controls:
- Document IDs can be hashed or replaced with pseudonyms as needed.
- Clients can configure data retention policies that purge identifying content after analysis is complete.
Intrusion/Threat Detection:
Question:
Does Luminoso conduct regular intrusion detection or threat monitoring? Are there any third-party audits or certifications (e.g., SOC 2) available?
Answer:
Luminoso has implemented controls that are grounded in the ISO 27001 standard and are compliant with SOC 2 security and availability principles.
Our API is only accessible through the use of Transport Layer Security (TLS), protecting our customers’ data in transit between our customers and our servers. Once customer data is on our servers, we implement additional safeguards, including firewalls, to ensure that only registered and authorized users in a customer’s organization are able to access the data and analysis results belonging to that organization.
Luminoso staff members have access to customer data only to the minimum extent necessary to perform our business functions.
Authenticated users of Luminoso’s application sites are issued locally stored tokens for the purpose of recording encrypted and signed authentication information; these tokens exist for a limited duration and do not record any confidential user or customer information.
Private Network Connectivity:
Question:
Is a private network (e.g., AWS PrivateLink or VPC) used to connect Luminoso’s AI services to customer data?
Answer:
Luminoso can deploy Daylight within a dedicated Virtual Private Cloud (VPC) hosted on Amazon Web Services (AWS) or the Google Cloud Platform (GCP) to ensure secure isolation and network-level protection for customer data.
Single-Tenant VPC Architecture:
Luminoso can provision single-tenant, logically isolated VPC environments, preventing cross-tenant data exposure. Each VPC is tailored to that client’s deployment and is isolated at the networking and access-control layers.
No Public Internet Exposure for Core Services:
Customer data and AI processing endpoints are only accessible within the secure VPC environment. Where integrations with external systems are required, these are controlled via whitelisted, secure connection methods (e.g., VPN, IP allowlisting).
Private Connectivity Options:
Luminoso supports optional configurations using AWS PrivateLink or customer-managed VPN tunnels for clients requiring direct private connections into their corporate environments. These are negotiated based on contractual or security needs.
Network Segmentation and Firewalls:
Internal services are segmented with strict security group policies, and all network traffic is governed by least-access firewall rules and intrusion detection controls.
Data in Transit Encryption:
All data transmitted within the VPC or across customer-facing endpoints is encrypted using TLS 1.2+, regardless of whether the connection is private or public.
Two-Factor Authentication (2FA):
Question:
Does Luminoso support 2FA for user access? If yes, could you share details on the implementation (e.g., SMS, authenticator app, etc.)?
Answer:
Luminoso can support 2FA for user access for Daylight clients hosted on a single-tenant cloud deployments that utilize integrated Single Sign-On (SSO) platforms that enforce 2FA policies at the identity provider level. All 2FA-enabled logins are logged and monitored as part of Luminoso’s broader security operations and access governance.
2FA is not supported for clients in multi-tenant cloud environments.
Helios Security
Does Helios use my data to train other Large Language Models?
No. Helios keeps your data private.
Helios does not store your data, nor is the data provided to Helios used to train any large language models.
Claude is a large language model developed by Anthropic. Amazon Bedrock is a cloud-based service from AWS that allows developers to access and use various foundation models, including Claude. In essence, Bedrock is a platform, and Claude is one of the models available on that platform. See the Bedrock FAQ page here.
Amazon Bedrock prioritizes data security and privacy for its clients using a multi-layered approach. Here are some key ways it guarantees data security:
- Data Isolation and Encryption:
Customer data is not used to train or improve base models: Customer inputs and outputs are not used for training AWS’s own models or shared with third-party model providers.
Encrypted in transit and at rest: Data used by Bedrock is encrypted while it’s being transmitted (in transit) using TLS 1.2 or higher, and also when it’s stored (at rest) using AWS Key Management Service (KMS). - Secure Connectivity and Access Control:
You can establish private network connections from your Amazon Virtual Private Cloud (VPC) to Amazon Bedrock using AWS PrivateLink, keeping your data traffic off the public internet.
AWS Identity and Access Management (IAM) allows you to define policies to restrict who can invoke specific models or access specific Bedrock resources. - Compliance and Responsible AI:
Amazon Bedrock supports common compliance standards like SOC, ISO, HIPAA, and GDPR.
Amazon Bedrock Guardrails help you implement safeguards for your generative AI applications. - Logging and Auditing:
Integrations with Amazon CloudWatch and AWS CloudTrail provide detailed logs for monitoring and auditing.
You can enable logging of model inputs and outputs for auditing. (We are currently not doing this)
In summary, Amazon Bedrock provides a secure environment for using LLMs through data isolation, encryption, access control, compliance, and responsible AI features. Remember, security is a shared responsibility, and you should follow AWS best practices for your specific use case.
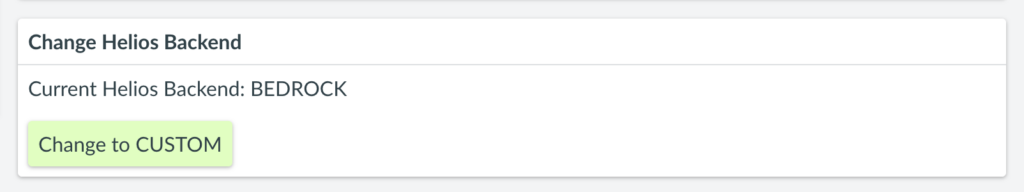
My organization uses our own LLM, can I use that to power Helios?
Yes. Contact your Luminoso success or account manager to discuss getting this set up. Once setup is complete, users may go to the Helios Backend from the Project Management page and “Change to CUSTOM”
How does Helios prevent responding with AI hallucinations, otherwise explained as providing false or misleading information?
The current version of the Helios Chatbot is a RAG (Retrieval Augment Generation) pipeline. By its design, RAGs are not prone to hallucinations.
The model responds to the customer query based on the context obtained during the Information Retrieval step of the pipeline. The Retrieval step doesn’t involve any genAI. It is a search through the dataset based on the query.
The model gets the query together with the result of the Retrieval step (a.k.a context) and generate the answer exclusively based on the context being provided. Hence, this step is called the Augmented Generation. This behavior is further reinforced by the system prompt explicitly instructing the model to only use the context to answer the query.